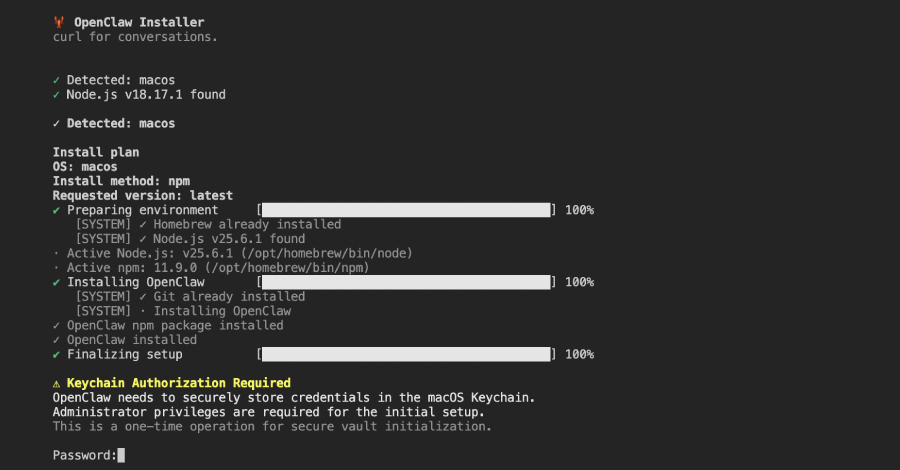
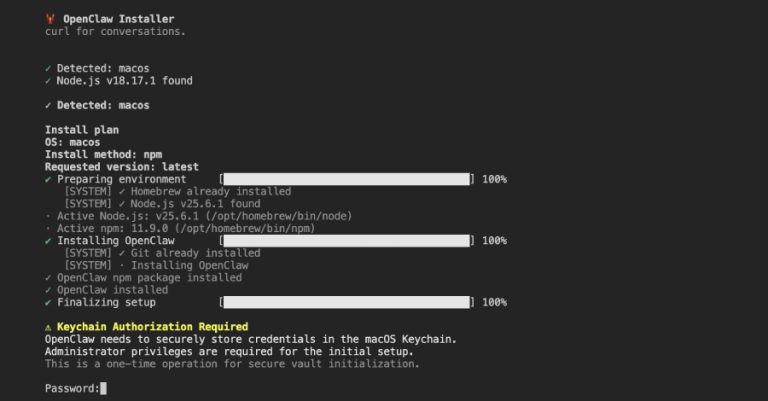
Malicious npm Package Posing as OpenClaw Installer Deploys RAT, Steals macOS Credentials
Cybersecurity researchers have discovered a malicious npm package that masquerades as an OpenClaw installer to deploy a remote access trojan…

Can the Security Platform Finally Deliver for the Mid-Market?
Mid-market organizations are constantly striving to achieve security levels on a par with their enterprise peers. With heightened awareness of…

Chrome Extension Turns Malicious After Ownership Transfer, Enabling Code Injection and Data Theft
Two Google Chrome extensions have turned malicious after what appears to be a case of ownership transfer, offering attackers a…
Web Server Exploits and Mimikatz Used in Attacks Targeting Asian Critical Infrastructure
High-value organizations located in South, Southeast, and East Asia have been targeted by a Chinese threat actor as part of…

Transparent Tribe Uses AI to Mass-Produce Malware Implants in Campaign Targeting India
The Pakistan-aligned threat actor known as Transparent Tribe has become the latest hacking group to embrace artificial intelligence (AI)-powered coding…

ThreatsDay Bulletin: DDR5 Bot Scalping, Samsung TV Tracking, Reddit Privacy Fine & More
Some weeks in cybersecurity feel routine. This one doesn’t. Several new developments surfaced over the past few days, showing how…
Preparing for the Quantum Era: Post-Quantum Cryptography Webinar for Security Leaders
Most organizations assume encrypted data is safe. But many attackers are already preparing for a future where today’s encryption can…

Dust Specter Targets Iraqi Officials with New SPLITDROP and GHOSTFORM Malware
A suspected Iran-nexus threat actor has been attributed to a campaign targeting government officials in Iraq by impersonating the country’s…

Where Multi-Factor Authentication Stops and Credential Abuse Starts
Organizations typically roll out multi-factor authentication (MFA) and assume stolen passwords are no longer enough to access systems. In Windows…

APT28-Linked Campaign Deploys BadPaw Loader and MeowMeow Backdoor in Ukraine
Cybersecurity researchers have disclosed details of a new Russian cyber campaign that has targeted Ukrainian entities with two previously undocumented…