Abandoned Sogou Zhuyin Update Server Hijacked, Weaponized in Taiwan Espionage Campaign
An abandoned update server associated with input method editor (IME) software Sogou Zhuyin was leveraged by threat actors as part…

An abandoned update server associated with input method editor (IME) software Sogou Zhuyin was leveraged by threat actors as part…
Amazon on Friday said it flagged and disrupted what it described as an opportunistic watering hole campaign orchestrated by the…

Click Studios, the developer of enterprise-focused password management solution Passwordstate, said it has released security updates to address an authentication…
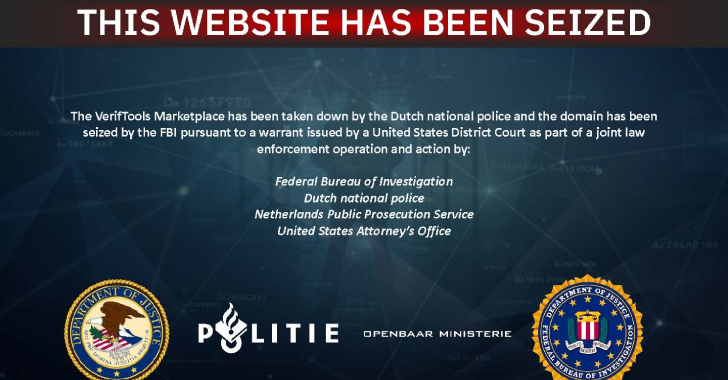
Authorities from the Netherlands and the United States have announced the dismantling of an illicit marketplace called VerifTools that peddled…

Google has revealed that the recent wave of attacks targeting Salesforce instances via Salesloft Drift is much broader in scope…

The China-linked advanced persistent threat (APT) actor known as Salt Typhoon has continued its attacks targeting networks across the world,…

Every day, businesses, teams, and project managers trust platforms like Trello, Asana, etc., to collaborate and manage tasks. But what…

The maintainers of the nx build system have alerted users to a supply chain attack that allowed attackers to publish…
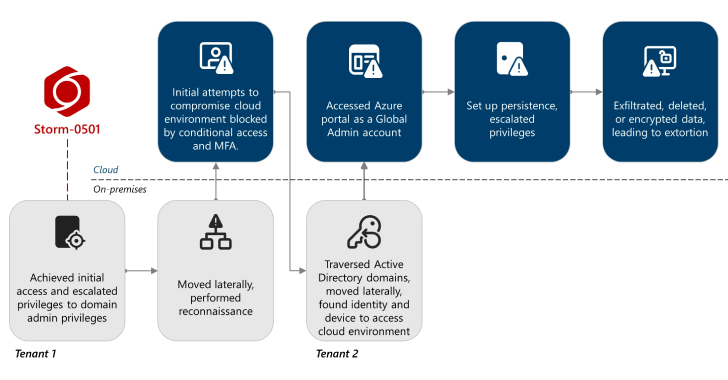
The financially motivated threat actor known as Storm-0501 has been observed refining its tactics to conduct data exfiltration and extortion…

Cybersecurity company ESET has disclosed that it discovered an artificial intelligence (AI)-powered ransomware variant codenamed PromptLock. Written in Golang, the…