
Fortra Releases Critical Patch for CVSS 10.0 GoAnywhere MFT Vulnerability
Fortra has disclosed details of a critical security flaw in GoAnywhere Managed File Transfer (MFT) software that could result in…

Fortra has disclosed details of a critical security flaw in GoAnywhere Managed File Transfer (MFT) software that could result in…

A proxy network known as REM Proxy is powered by malware known as SystemBC, offering about 80% of the botnet…

Run by the team at workflow orchestration and AI platform Tines, the Tines library features over 1,000 pre-built workflows shared…

Cybersecurity researchers have discerned evidence of two Russian hacking groups Gamaredon and Turla collaborating together to target and co-comprise Ukrainian…

Law enforcement authorities in the U.K. have arrested two teen members of the Scattered Spider hacking group in connection with…

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday released details of two sets of malware that were discovered…

SonicWall is urging customers to reset credentials after their firewall configuration backup files were exposed in a security breach impacting…

Generative AI has gone from a curiosity to a cornerstone of enterprise productivity in just a few short years. From…

The U.S. Department of Justice (DoJ) on Tuesday resentenced the former administrator of BreachForums to three years in prison in…
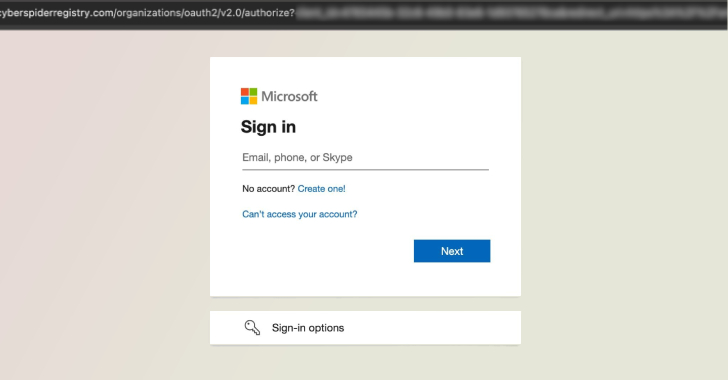
Microsoft’s Digital Crimes Unit said it teamed up with Cloudflare to coordinate the seizure of 338 domains used by RaccoonO365,…