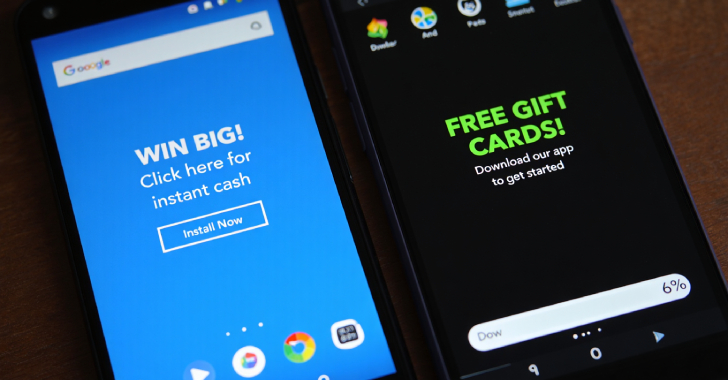
SlopAds Fraud Ring Exploits 224 Android Apps to Drive 2.3 Billion Daily Ad Bids
A massive ad fraud and click fraud operation dubbed SlopAds ran a cluster of 224 apps, collectively attracting 38 million…

A massive ad fraud and click fraud operation dubbed SlopAds ran a cluster of 224 apps, collectively attracting 38 million…

AI agents are rapidly becoming a core part of the enterprise, being embedded across enterprise workflows, operating with autonomy, and…

Apple on Monday backported fixes for a recently patched security flaw that has been actively exploited in the wild. The…
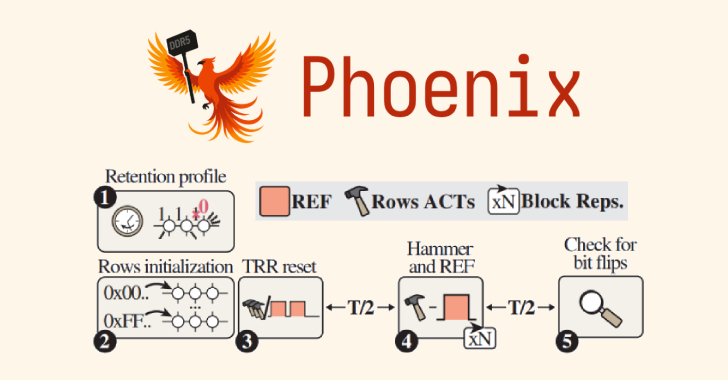
A team of academics from ETH Zürich and Google has discovered a new variant of a RowHammer attack targeting Double…

Cybersecurity researchers have flagged a fresh software supply chain attack targeting the npm registry that has affected more than 40…

The China-aligned threat actor known as Mustang Panda has been observed using an updated version of a backdoor called TONESHELL…

The U.S. Federal Bureau of Investigation (FBI) has issued a flash alert to release indicators of compromise (IoCs) associated with…
Samsung has released its monthly security updates for Android, including a fix for a security vulnerability that it said has…
The security landscape for cloud-native applications is undergoing a profound transformation. Containers, Kubernetes, and serverless technologies are now the default…

Cybersecurity researchers have disclosed two new campaigns that are serving fake browser extensions using malicious ads and fake websites to…