
DarkSpectre Browser Extension Campaigns Exposed After Impacting 8.8 Million Users Worldwide
The threat actor behind two malicious browser extension campaigns, ShadyPanda and GhostPoster, has been attributed to a third attack campaign…

The threat actor behind two malicious browser extension campaigns, ShadyPanda and GhostPoster, has been attributed to a third attack campaign…

Cybersecurity researchers have disclosed details of what appears to be a new strain of Shai Hulud on the npm registry…

IBM has disclosed details of a critical security flaw in API Connect that could allow attackers to gain remote access…

The Chinese hacking group known as Mustang Panda has leveraged a previously undocumented kernel-mode rootkit driver to deliver a new…

Cybersecurity researchers have disclosed details of what has been described as a “sustained and targeted” spear-phishing campaign that has published…
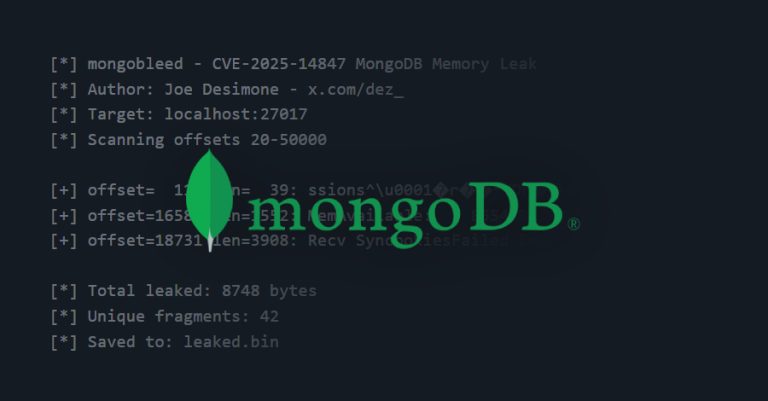
A recently disclosed security vulnerability in MongoDB has come under active exploitation in the wild, with over 87,000 potentially susceptible…
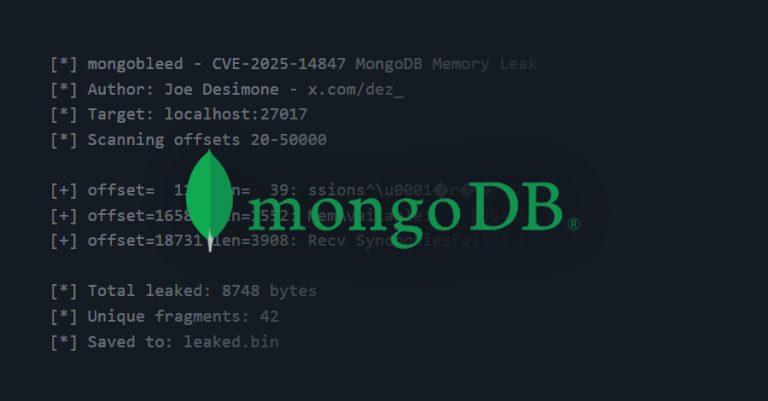
A recently disclosed security vulnerability in MongoDB has come under active exploitation in the wild, with over 87,000 potentially susceptible…

A critical security flaw has been disclosed in LangChain Core that could be exploited by an attacker to steal sensitive…

It’s getting harder to tell where normal tech ends and malicious intent begins. Attackers are no longer just breaking in…

The encrypted vault backups stolen from the 2022 LastPass data breach have enabled bad actors to take advantage of weak…