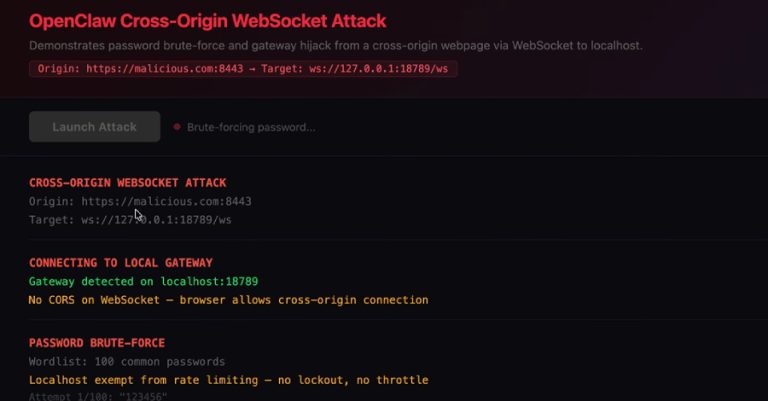
ClawJacked Flaw Lets Malicious Sites Hijack Local OpenClaw AI Agents via WebSocket
OpenClaw has fixed a high-severity security issue that, if successfully exploited, could have allowed a malicious website to connect to…

OpenClaw has fixed a high-severity security issue that, if successfully exploited, could have allowed a malicious website to connect to…

The Shadowserver Foundation has revealed that over 900 Sangoma FreePBX instances still remain infected with web shells as part of…

Threat actors are luring unsuspecting users into running trojanized gaming utilities that are distributed via browsers and chat platforms to…

A newly disclosed maximum-severity security flaw in Cisco Catalyst SD-WAN Controller (formerly vSmart) and Catalyst SD-WAN Manager (formerly vManage) has…
Cybersecurity researchers have disclosed multiple security vulnerabilities in Anthropic’s Claude Code, an artificial intelligence (AI)-powered coding assistant, that could result…

The notorious cybercrime collective known as Scattered LAPSUS$ Hunters (SLH) has been observed offering financial incentives to recruit women to…

Why automating sensitive data transfers is now a mission-critical priority More than half of national security organizations still rely on…

Most identity programs still prioritize work the way they prioritize IT tickets: by volume, loudness, or “what failed a control…

Cybersecurity researchers have disclosed details of a new cryptojacking campaign that uses pirated software bundles as lures to deploy a…

Security news rarely moves in a straight line. This week, it feels more like a series of sharp turns, some…