
MuddyWater Launches RustyWater RAT via Spear-Phishing Across Middle East Sectors
The Iranian threat actor known as MuddyWater has been attributed to a spear-phishing campaign targeting diplomatic, maritime, financial, and telecom…

The Iranian threat actor known as MuddyWater has been attributed to a spear-phishing campaign targeting diplomatic, maritime, financial, and telecom…

Europol on Friday announced the arrest of 34 individuals in Spain who are alleged to be part of an international…

Trend Micro has released security updates to address multiple security vulnerabilities impacting on-premise versions of Apex Central for Windows, including…
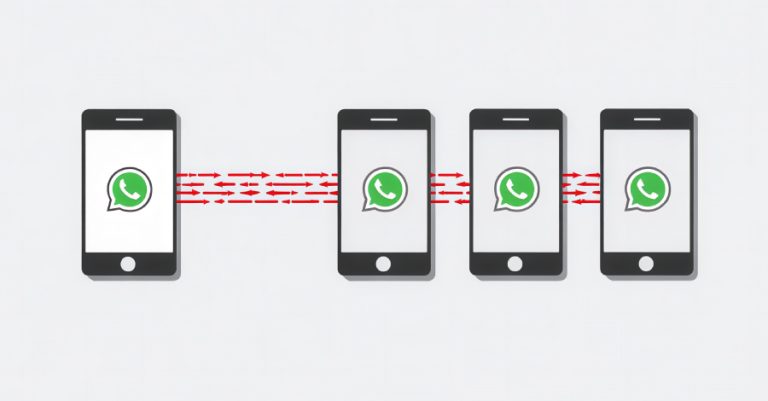
Cybersecurity researchers have disclosed details of a new campaign that uses WhatsApp as a distribution vector for a Windows banking…

Chainguard, the trusted source for open source, has a unique view into how modern organizations actually consume open source software…

A newly discovered critical security flaw in legacy D-Link DSL gateway routers has come under active exploitation in the wild….
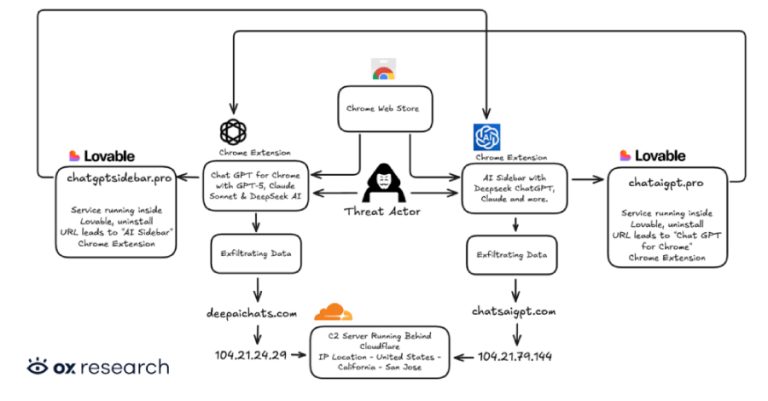
Cybersecurity researchers have discovered two new malicious extensions on the Chrome Web Store that are designed to exfiltrate OpenAI ChatGPT…
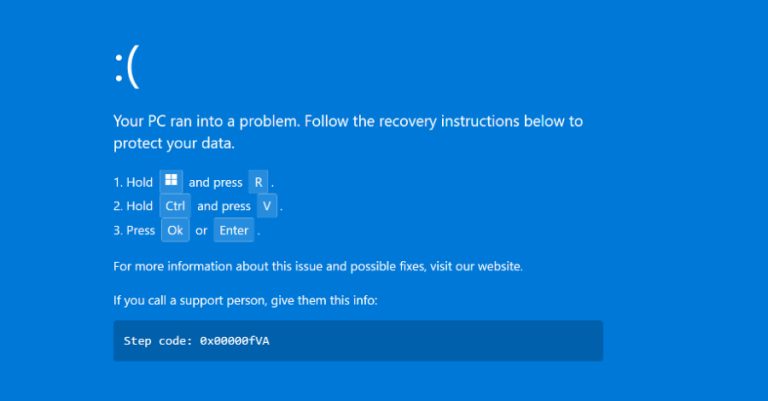
Source: Securonix Cybersecurity researchers have disclosed details of a new campaign dubbed PHALT#BLYX that has leveraged ClickFix-style lures to display…

The Invisible Half of the Identity Universe Identity used to live in one place – an LDAP directory, an HR…

A new critical security vulnerability has been disclosed in n8n, an open-source workflow automation platform, that could enable an authenticated…