
Compromised dYdX npm and PyPI Packages Deliver Wallet Stealers and RAT Malware
Cybersecurity researchers have discovered a new supply chain attack in which legitimate packages on npm and the Python Package Index…

Cybersecurity researchers have discovered a new supply chain attack in which legitimate packages on npm and the Python Package Index…
Today’s “AI everywhere” reality is woven into everyday workflows across the enterprise, embedded in SaaS platforms, browsers, copilots, extensions, and…
A new, critical security vulnerability has been disclosed in the n8n workflow automation platform that, if successfully exploited, could result…

Threat actors affiliated with China have been attributed to a fresh set of cyber espionage campaigns targeting government and law…
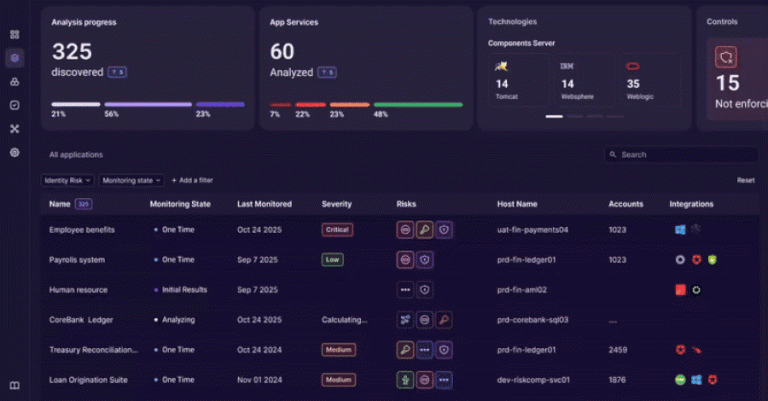
An innovative approach to discovering, analyzing, and governing identity usage beyond traditional IAM controls. The Challenge: Identity Lives Outside the…
![[Webinar] The Smarter SOC Blueprint: Learn What to Build, Buy, and Automate](https://hackvolt.com/wp-content/uploads/2026/02/preview-4-768x401.jpg)
Most security teams today are buried under tools. Too many dashboards. Too much noise. Not enough real progress. Every vendor…

Threat actors have been observed exploiting a critical security flaw impacting the Metro Development Server in the popular “@react-native-community/cli” npm…

The Russia-linked state-sponsored threat actor known as APT28 (aka UAC-0001) has been attributed to attacks exploiting a newly disclosed security…

A China-linked threat actor known as Lotus Blossom has been attributed with medium confidence to the recently discovered compromise of…

Microsoft has announced a three-phase approach to phase out New Technology LAN Manager (NTLM) as part of its efforts to…