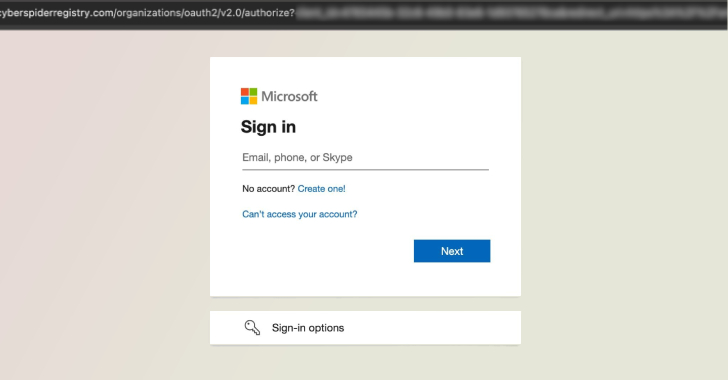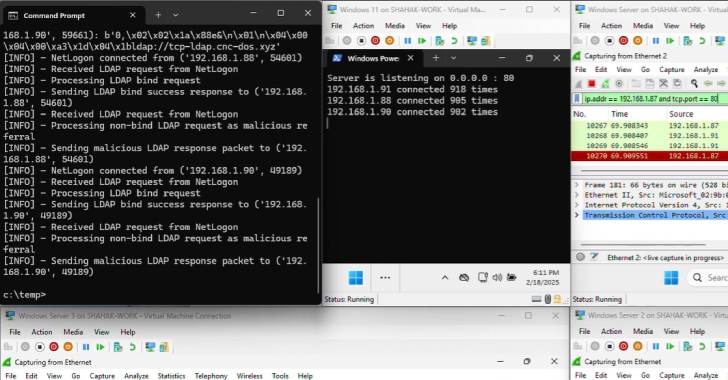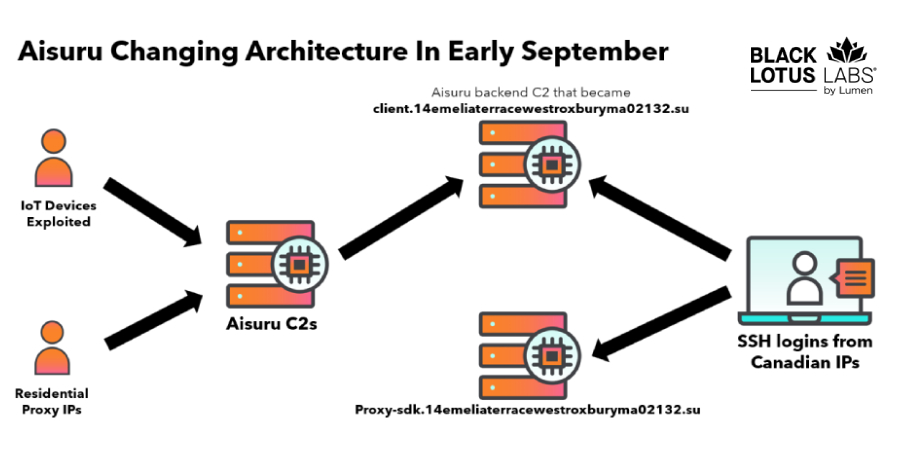
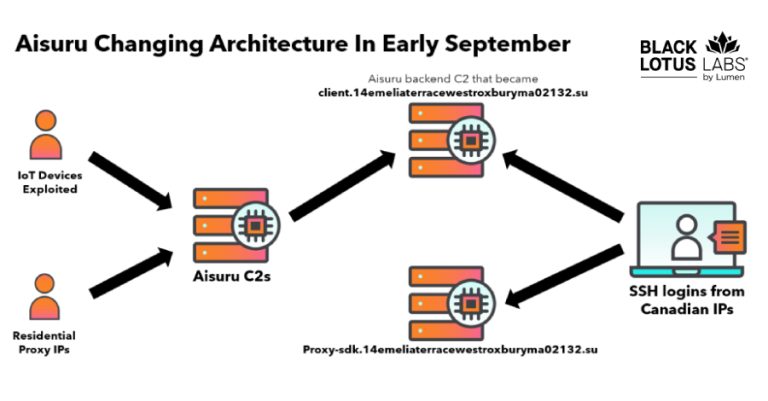
Researchers Null-Route Over 550 Kimwolf and Aisuru Botnet Command Servers
The Black Lotus Labs team at Lumen Technologies said it null-routed traffic to more than 550 command-and-control (C2) nodes associated…
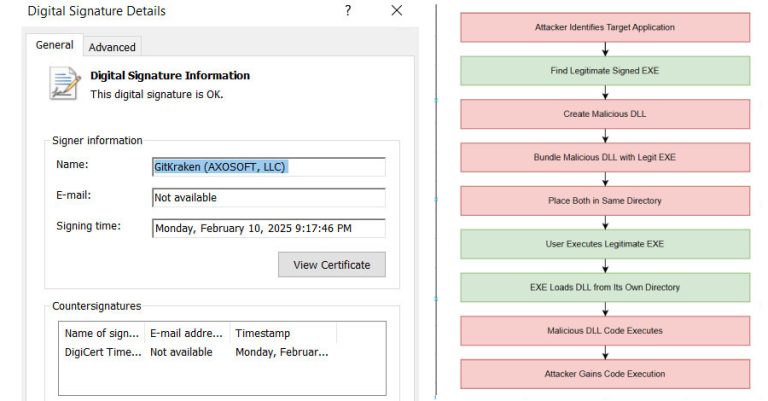
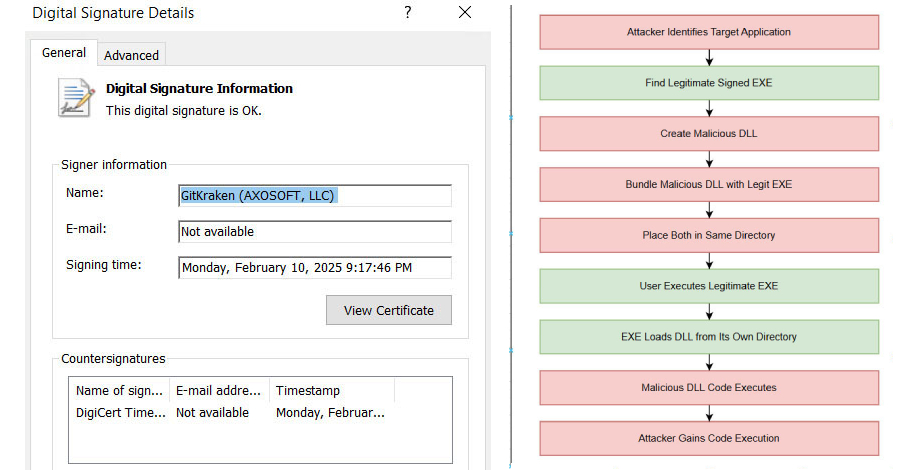
Hackers Exploit c-ares DLL Side-Loading to Bypass Security and Deploy Malware
Security experts have disclosed details of an active malware campaign that’s exploiting a DLL side-loading vulnerability in a legitimate binary…

New Research: 64% of 3rd-Party Applications Access Sensitive Data Without Justification
Research analyzing 4,700 leading websites reveals that 64% of third-party applications now access sensitive data without business justification, up from…

Malicious Chrome Extension Steals MEXC API Keys by Masquerading as Trading Tool
Cybersecurity researchers have disclosed details of a malicious Google Chrome extension that’s capable of stealing API keys associated with MEXC,…

ServiceNow Patches Critical AI Platform Flaw Allowing Unauthenticated User Impersonation
ServiceNow has disclosed details of a now-patched critical security flaw impacting its ServiceNow AI Platform that could enable an unauthenticated…

What Should We Learn From How Attackers Leveraged AI in 2025?
Old Playbook, New Scale: While defenders are chasing trends, attackers are optimizing the basics The security industry loves talking about…

⚡ Weekly Recap: AI Automation Exploits, Telecom Espionage, Prompt Poaching & More
This week made one thing clear: small oversights can spiral fast. Tools meant to save time and reduce friction turned…

MuddyWater Launches RustyWater RAT via Spear-Phishing Across Middle East Sectors
The Iranian threat actor known as MuddyWater has been attributed to a spear-phishing campaign targeting diplomatic, maritime, financial, and telecom…

Europol Arrests 34 Black Axe Members in Spain Over €5.9M Fraud and Organized Crime
Europol on Friday announced the arrest of 34 individuals in Spain who are alleged to be part of an international…

Trend Micro Apex Central RCE Flaw Scores 9.8 CVSS in On-Prem Windows Versions
Trend Micro has released security updates to address multiple security vulnerabilities impacting on-premise versions of Apex Central for Windows, including…