
Critical WordPress Modular DS Plugin Flaw Actively Exploited to Gain Admin Access
A maximum-severity security flaw in a WordPress plugin called Modular DS has come under active exploitation in the wild, according…

A maximum-severity security flaw in a WordPress plugin called Modular DS has come under active exploitation in the wild, according…

It’s 2026, yet many SOCs are still operating the way they did years ago, using tools and processes designed for…

Microsoft on Wednesday announced that it has taken a “coordinated legal action” in the U.S. and the U.K. to disrupt…
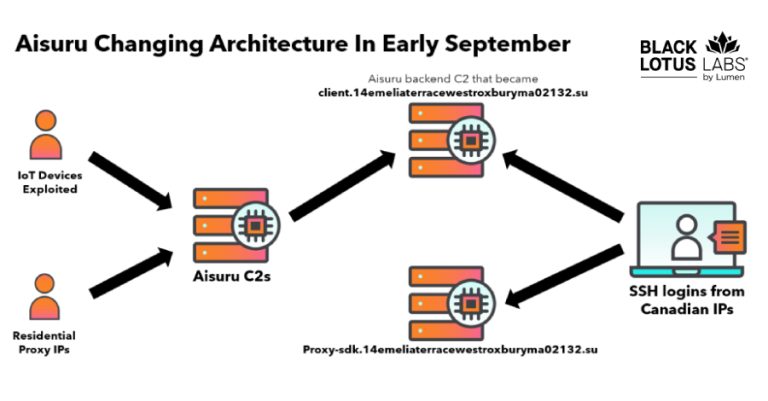
The Black Lotus Labs team at Lumen Technologies said it null-routed traffic to more than 550 command-and-control (C2) nodes associated…
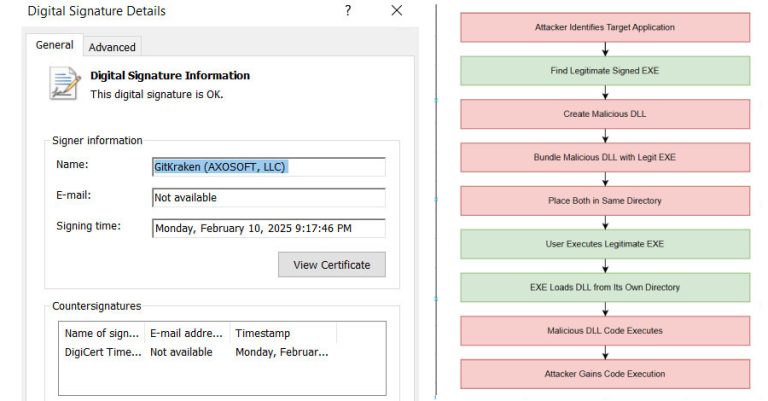
Security experts have disclosed details of an active malware campaign that’s exploiting a DLL side-loading vulnerability in a legitimate binary…

Research analyzing 4,700 leading websites reveals that 64% of third-party applications now access sensitive data without business justification, up from…

Cybersecurity researchers have disclosed details of a malicious Google Chrome extension that’s capable of stealing API keys associated with MEXC,…

Old Playbook, New Scale: While defenders are chasing trends, attackers are optimizing the basics The security industry loves talking about…

ServiceNow has disclosed details of a now-patched critical security flaw impacting its ServiceNow AI Platform that could enable an unauthenticated…

This week made one thing clear: small oversights can spiral fast. Tools meant to save time and reduce friction turned…