
Bitfinex Hack Convict Ilya Lichtenstein Released Early Under U.S. First Step Act
Ilya Lichtenstein, who was sentenced to prison last year for money laundering charges in connection with his role in the…

Ilya Lichtenstein, who was sentenced to prison last year for money laundering charges in connection with his role in the…

The threat actor known as Transparent Tribe has been attributed to a fresh set of attacks targeting Indian governmental, academic,…

Cybersecurity researchers have disclosed details of a persistent nine-month-long campaign that has targeted Internet of Things (IoT) devices and web…

The threat actor behind two malicious browser extension campaigns, ShadyPanda and GhostPoster, has been attributed to a third attack campaign…

IBM has disclosed details of a critical security flaw in API Connect that could allow attackers to gain remote access…

Cybersecurity researchers have disclosed details of what appears to be a new strain of Shai Hulud on the npm registry…

The Chinese hacking group known as Mustang Panda has leveraged a previously undocumented kernel-mode rootkit driver to deliver a new…
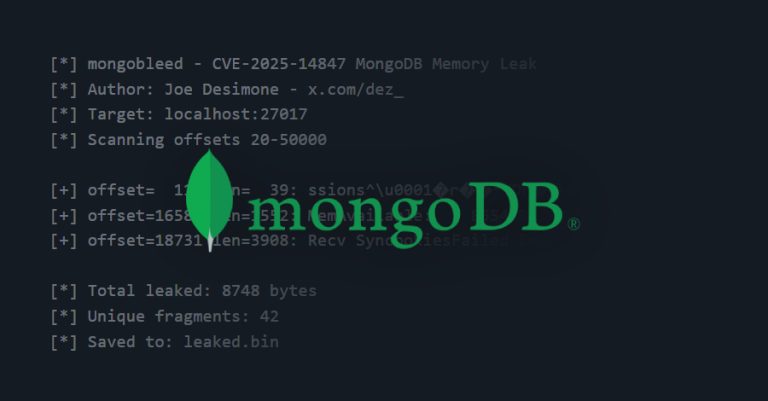
A recently disclosed security vulnerability in MongoDB has come under active exploitation in the wild, with over 87,000 potentially susceptible…

Cybersecurity researchers have disclosed details of what has been described as a “sustained and targeted” spear-phishing campaign that has published…
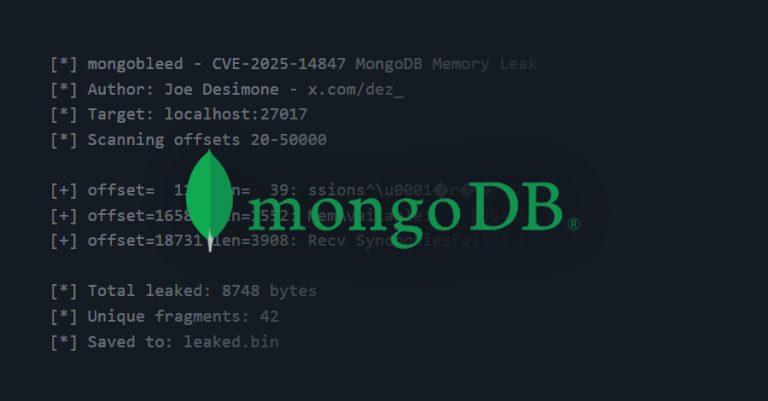
A recently disclosed security vulnerability in MongoDB has come under active exploitation in the wild, with over 87,000 potentially susceptible…