
CISA Flags Critical ASUS Live Update Flaw After Evidence of Active Exploitation
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a critical flaw impacting ASUS Live Update to its…

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a critical flaw impacting ASUS Live Update to its…

Cisco has alerted users of a maximum-severity zero-day flaw in Cisco AsyncOS software that has been actively exploited by a…
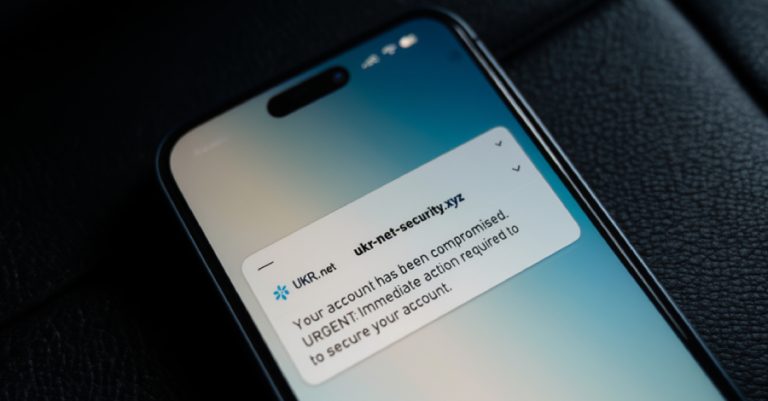
The Russian state-sponsored threat actor known as APT28 has been attributed to what has been described as a “sustained” credential-harvesting…

The threat actor known as Jewelbug has been increasingly focusing on government targets in Europe since July 2025, even as…

Modern security teams often feel like they’re driving through fog with failing headlights. Threats accelerate, alerts multiply, and SOCs struggle…

AI-assisted coding and AI app generation platforms have created an unprecedented surge in software development. Companies are now facing rapid…

Threat actors have begun to exploit two newly disclosed security flaws in Fortinet FortiGate devices, less than a week after…

The security vulnerability known as React2Shell is being exploited by threat actors to deliver malware families like KSwapDoor and ZnDoor,…
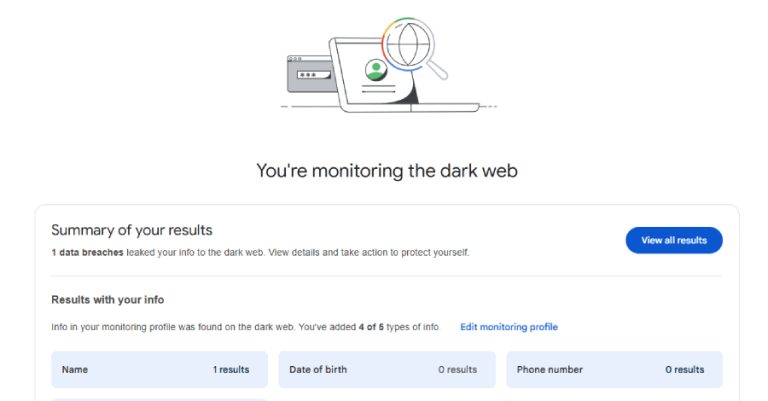
Google has announced that it’s discontinuing its dark web report tool in February 2026, less than two years after it…

Multiple security vulnerabilities have been disclosed in the open-source private branch exchange (PBX) platform FreePBX, including a critical flaw that…