
How Exposed Endpoints Increase Risk Across LLM Infrastructure
As more organizations run their own Large Language Models (LLMs), they are also deploying more internal services and Application Programming…

As more organizations run their own Large Language Models (LLMs), they are also deploying more internal services and Application Programming…
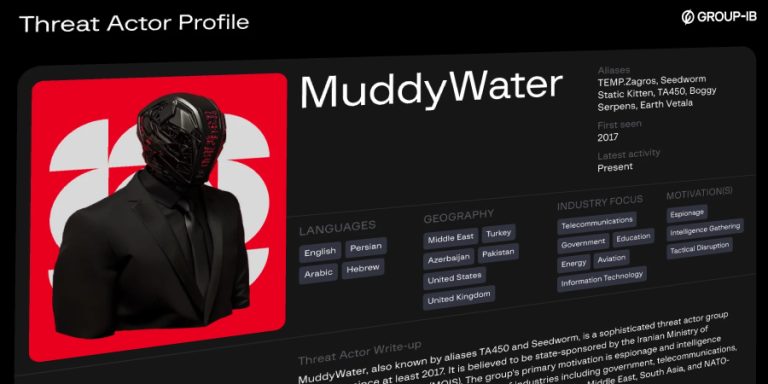
The Iranian hacking group known as MuddyWater (aka Earth Vetala, Mango Sandstorm, and MUDDYCOAST) has targeted several organizations and individuals…

A Russian-speaking, financially motivated threat actor has been observed taking advantage of commercial generative artificial intelligence (AI) services to compromise…
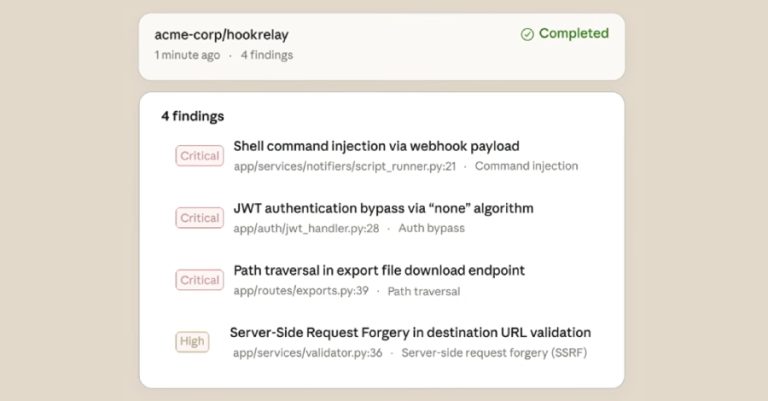
Artificial intelligence (AI) company Anthropic has begun to roll out a new security feature for Claude Code that can scan…

In yet another software supply chain attack, the open-source, artificial intelligence (AI)-powered coding assistant Cline CLI was updated to stealthily…

The U.S. Federal Bureau of Investigation (FBI) has warned of an increase in ATM jackpotting incidents across the country, leading…

Two former Google engineers and one of their husbands have been indicted in the U.S. for allegedly committing trade secret…

The cyber threat space doesn’t pause, and this week makes that clear. New risks, new tactics, and new security gaps…

Cybersecurity researchers have disclosed details of a new Android trojan called Massiv that’s designed to facilitate device takeover (DTO) attacks…

Cybersecurity researchers have disclosed details of a new campaign dubbed CRESCENTHARVEST, likely targeting supporters of Iran’s ongoing protests to conduct…