
Why Your Security Culture is Critical to Mitigating Cyber Risk
After two decades of developing increasingly mature security architectures, organizations are running up against a hard truth: tools and technologies…

After two decades of developing increasingly mature security architectures, organizations are running up against a hard truth: tools and technologies…

The U.K. government has apparently abandoned its plans to force Apple to weaken encryption protections and include a backdoor that…
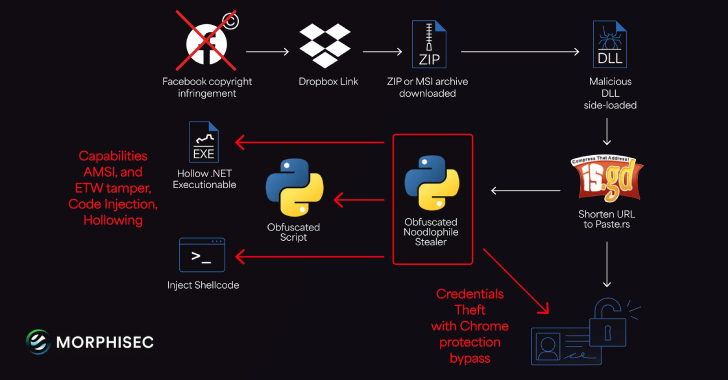
The threat actors behind the Noodlophile malware are leveraging spear-phishing emails and updated delivery mechanisms to deploy the information stealer…

Organizations handling various forms of sensitive data or personally identifiable information (PII) require adherence to regulatory compliance standards and frameworks….

The threat actor known as EncryptHub is continuing to exploit a now-patched security flaw impacting Microsoft Windows to deliver malicious…
We used to think of privacy as a perimeter problem: about walls and locks, permissions, and policies. But in a…
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) on Thursday renewed sanctions against Russian cryptocurrency exchange…

You check that the windows are shut before leaving home. Return to the kitchen to verify that the oven and…

Cybersecurity researchers have disclosed a new Android trojan called PhantomCard that abuses near-field communication (NFC) to conduct relay attacks for…

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added two security flaws impacting N-able N-central to its Known…