
Password Reuse in Disguise: An Often-Missed Risky Workaround
When security teams discuss credential-related risk, the focus typically falls on threats such as phishing, malware, or ransomware. These attack…

When security teams discuss credential-related risk, the focus typically falls on threats such as phishing, malware, or ransomware. These attack…
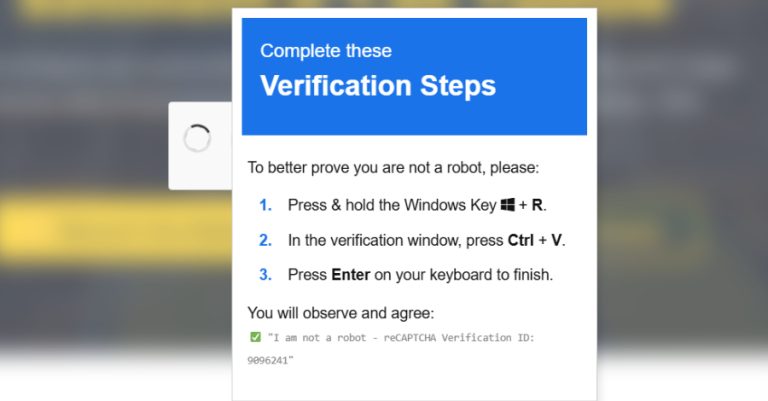
Cybersecurity researchers have disclosed details of a new campaign that combines ClickFix-style fake CAPTCHAs with a signed Microsoft Application Virtualization…

Cybersecurity researchers have discovered an ongoing campaign that’s targeting Indian users with a multi-stage backdoor as part of a suspected…

If there’s a constant in cybersecurity, it’s that adversaries are always innovating. The rise of offensive AI is transforming attack…
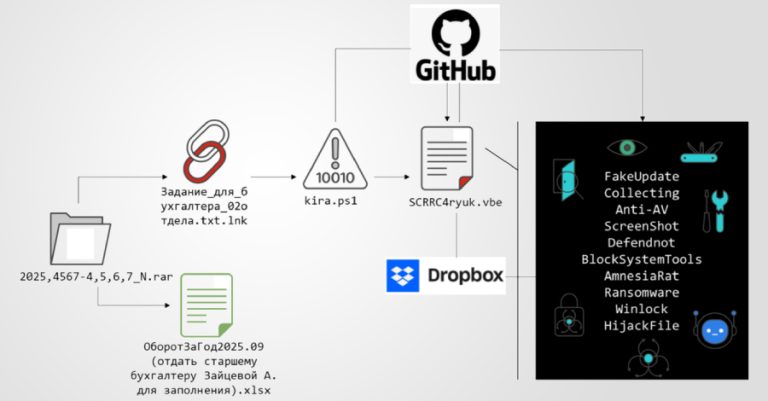
A new multi-stage phishing campaign has been observed targeting users in Russia with ransomware and a remote access trojan called…

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added a critical security flaw affecting Broadcom VMware vCenter Server…

AI agents are accelerating how work gets done. They schedule meetings, access data, trigger workflows, write code, and take action…

The Russian nation-state hacking group known as Sandworm has been attributed to what has been described as the “largest cyber…

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added four security flaws to its Known Exploited Vulnerabilities (KEV)…

Fortinet has officially confirmed that it’s working to completely plug a FortiCloud SSO authentication bypass vulnerability following reports of fresh…