
⚡ Weekly Recap: F5 Breached, Linux Rootkits, Pixnapping Attack, EtherHiding & More
It’s easy to think your defenses are solid — until you realize attackers have been inside them the whole time….

It’s easy to think your defenses are solid — until you realize attackers have been inside them the whole time….

Europol on Friday announced the disruption of a sophisticated cybercrime-as-a-service (CaaS) platform that operated a SIM farm and enabled its…

Cybersecurity researchers have shed light on a new campaign that has likely targeted the Russian automobile and e-commerce sectors with…

The threat actors behind a malware family known as Winos 4.0 (aka ValleyRAT) have expanded their targeting footprint from China…

The danger isn’t that AI agents have bad days — it’s that they never do. They execute faithfully, even when…
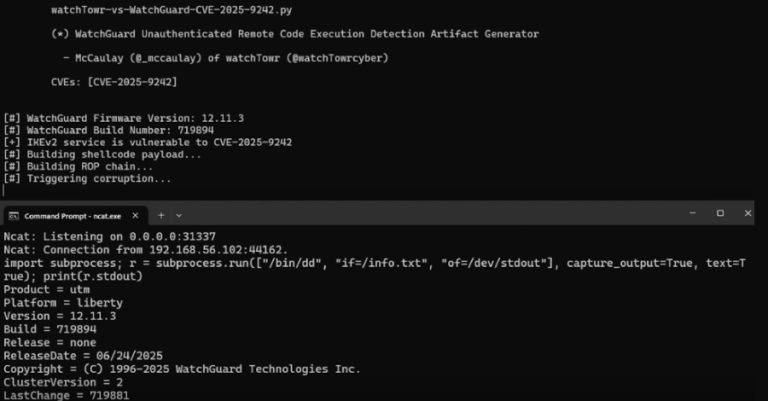
Cybersecurity researchers have disclosed details of a recently patched critical security flaw in WatchGuard Fireware that could allow unauthenticated attackers…

Microsoft on Thursday disclosed that it revoked more than 200 certificates used by a threat actor it tracks as Vanilla…

The online world is changing fast. Every week, new scams, hacks, and tricks show how easy it’s become to turn…

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a critical security flaw impacting Adobe Experience Manager to…

U.S. cybersecurity company F5 on Wednesday disclosed that unidentified threat actors broke into its systems and stole files containing some…